With the curtain having now fallen on CES 2023 in Las Vegas, it is clear that consumer technology has a truly exciting future ahead of it.
Trends like accessible gaming hardware, laptop-charging bike desks, and artificially intelligent ovens may have stolen the spotlight, but there were hundreds of other technologies showcased at the event.
Although many of these might have gone under the radar, some will nevertheless play a hugely important role in shaping the future of consumer technology. For example, ARMv9 – the latest iteration of ARM’s processor architecture for Internet of Things [IoT] devices – has helped to power many of the innovations that were unveiled at CES.
A brief history of ARM
Before going any further into what ARMv9 actually is, and the significance of its role in IoT technology, it is first important to establish what ARM itself is, and the journey that the architecture has gone on to date.
In broad terms, ARM architecture is a family of central processor units [CPUs] developed by ARM Holdings. Based on the reduced instruction set computing architecture known as RISC, ARM processors are used across a wide range of consumer devices, from digital TVs and set-top boxes, to smartphones and mobile computers. Since 2014, ARM has been the most widely used 32-bit instruction set architecture in the world.
With technology playing an increasingly central role in the world of business as well as everyday life, users require a smooth experience from their connected devices.
To achieve this, most gadgets are now fitted with embedded processors that are not only compact in size, but also help to ensure that consumer devices perform as efficiently as they should.
While there are a variety of embedded architectures that manufacturers can choose to implement into their devices, ARM is by far the most popular, accounting for approximately 95 per cent of all smartphone processors.
While the first ARM instruction set version launched alongside the initial ARM processor back in 1985, the architecture has evolved significantly since then.
To begin with, each of ARM’s new processor families was named chronologically, starting with ARM1, and running up to ARM11 in 2002. However, when the Cortex processor family was introduced in 2005, the naming convention was changed.
This means that each new processor is now assigned the name ‘Cortex’, with a corresponding letter and number following it.
While ARM’s naming conventions may be confusing for anyone who isn’t a software engineer, the key thing to remember is that ARM1 and ARM11, etc., are processor families, whereas ARMv8 and ARMv9, etc., are the architectures that those processors are designed from.
What is ARMv9?
Coming back to ARMv9 itself, this iteration of the company’s processor architecture was revealed in March 2021. In announcing ARMv9, ARM has set out its vision for what it hopes will be the computing platform for the next 300 billion chips across the next decade.
Indeed, ARM has claimed that the new architecture will give ‘CPU performance increases of more than 30% over the next two generations of mobile and infrastructure CPUs’.
Since launching ARMv9, ARM has announced a range of extensions to the architecture that are designed to build upon the offering by adding to the instructions implemented within the instruction set.
If ARMv8 is anything to go by, it is likely that we will see even more extensions implemented across ARMv9’s lifetime. However, these are the key features of ARMv9 as it stands.
Hypervisor support in the secure world
If hypervisors were enough to meet the security requirements of system designers, ARM would never have needed TrustZone Technology, which provides a cost-effective methodology to isolate security critical components in a system. This is done by hardware separating a rich operating system from a smaller secure operating system.
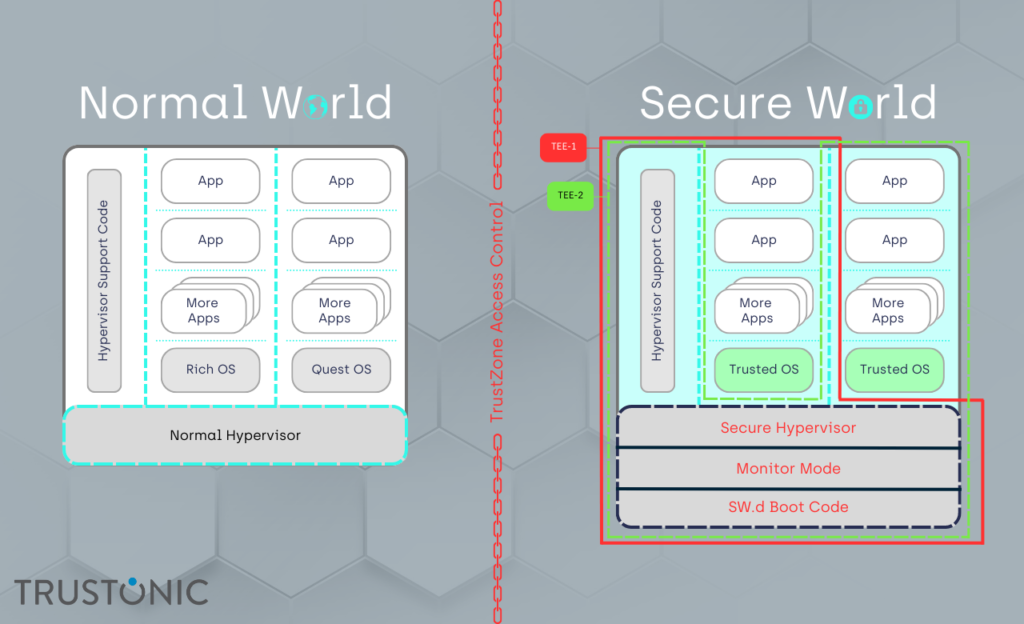
However, TrustZone was first introduced in 2004, and the technology has moved on significantly since then.
In 2023, hypervisors can make use of System Memory Management Units [SMMUs] that provide TrustZone-like isolation in the System on a Chip [SoC] design. Consequently, ARM has introduced hypervisor support to the secure world.
This represents a positive step forward, provided the same system level isolation within the Trusted Execution Environment [TEE] of the device is maintained, and the hypervisors are securely written.
Pointer Authentication Codes
One of ARMv9’s central features is pointer authentication codes [PAC].
The pointer authentication scheme introduced by ARM as part of AArch64 ARMv8-A is designed to make it considerably harder for an attacker to modify protected pointers in memory without being detected.
It works by offering a special CPU instruction to add a cryptographic signature – or PAC – to unused, high-order bits of a pointer before storing the pointer. An additional instruction removes and authenticates the signature once it has read the pointer back from memory.
Any change to the stored value between the write and the read then invalidates the signature, which the CPU interprets as memory corruption.
Consequently, the CPU sets a high-order bit in the pointer, making it invalid and causing the device to crash. In essence, PAC plays an integral role in ensuring that devices are protected from, and resilient to, attacks.
In PAC, which was introduced with ARMv8.3, ARM added meta data to distinguish five pointer types – two for data, two for code, and one for general purpose.
Misuse of these pointer types causes an exception, which then hardens the code base against attacks like Return-Orientated Programming [ROP] and Jump-Orientated Programming [JOP].
Branch Target Identification
ARM also included Branch Target Identification [BTI] as part of ARMv8.5’s security extensions, which has carried over into ARMv9. This provides Control Flow Integrity [CFI] around indirect branches and their targets, thereby assisting in limiting the number of JOP attacks against a device.
Branch Target Instructions [BTIs] are included within BTI itself. Also known as ‘landing pads’, these allow for processors to be configured so that indirect branches only allow target landing pad instructions.
If the target of an indirect branch is not a landing pad, a Branch Target Exception is generated. This is designed to prevent attackers from jumping into a code segment, given that only valid entry points are permitted.
As a result, the potential for attacks through bypassing function parameter checking is greatly mitigated.
Privileged Access Never
Known as PAN, Privileged Access Never was introduced in response to vulnerabilities detected within the ARMv8 64-bit specification’s memory access protections. Its purpose is to prevent privileged access to user data unless it is explicitly enabled as a security mechanism to protect against possible attacks.
This is achieved by enabling kernel-mode – or the hypervisor – to block its own access to address areas. While this may seem like a strange approach, it does means that, in the event that an attack does manage to break through the defences of the kernel, the repercussions are limited significantly.
Vector instructions
ARM has introduced a wide range of new technologies in the area of Vector support. Vector-based maths is critical in high-speed computing, particularly in areas like image analysis, biometric security, and cryptography.
Vector instructions with ARM architecture began with ARM NEON and Single Instruction/Multiple Data [SIMD] instructions, and these were enhanced throughout ARMv8 with the Scalable Vector Extension [SVE].
ARMv9 then introduced SVE2, which was extended further with the Scalable Matrix Extension [SME] in ARMv9.2 Furthermore, ARM also added in some new General Matrix Multiply [GEMM] instructions in a bid to reduce bandwidth memory.
Effectively, all of these technologies are designed to provide better ways for manipulating large ‘numbers’ – i.e., images or blocks of encrypted data.
Confidential Compute, aka ‘Realm Memory Extension’
According to ARM, the addition of its Confidential Compute feature within ARMv9 helps to provide hardware roots for isolation, confidentiality, and authenticity that can rival TrustZone Technology.
Confidential Compute is designed to protect portions of code and data from access or modification while it is being used, even from authorised software, by putting computation into hardware-based security.
The Confidential Compute Architecture [CCA] operates on a concept called Realms, which works in a region separate from secure and non-secure environments. This means that Realms is capable of protecting sensitive data and code from the rest of a system, irrespective of whether it is in-use, at rest, or in transit.
Summary
From a Trustonic perspective, the two most significant features within ARMv9 are its Memory Tagging Extension [MTE] and its Secure Hypervisor leading to the FF-A interface [Firmware Framework for Cortex-A].
This is because these features both form key parts of our Kinibi 600 TEE. Given the complexities of MTE and FF-A, we will be taking a deeper dive into these features in our next blog on ARMv9, explaining why we decided to implement them into Kinibi 600.
We are proud to have established ourselves as a key part of the ARM ecosystem. In adopting ARMv9, we have made significant advancements to our technology, having implemented many key features into our TEE that were not expected to be widely available until well into 2023/24.
Because we are so ahead of the curve when it comes to ARMv9, we stand in an incredibly strong position to support our clients in their journey towards embracing the architecture. What’s more, considering we have already taken customers through ARMv7 and ARMv8, we have proven ourselves to be a safe pair of hands when it comes to moving towards handling different CPU architectures.
As far as ARMv9 itself is concerned, it is not, in fact, as monumental a change as many Original Equipment Manufacturers [OEMs] may have been led to believe it is.
Despite this, it does bring a number of exciting new features. For example, the architecture has introduced crucial security-related technologies that have helped to harden the software and hardware environment over the ARMv8 offering.
Direct improvements have come in the form of BTI, PAC, and MTE, etc., while indirect enablers like the improvements to vector capability have assisted in strengthening the technology.
Given its complexities, ARMv9 can be difficult to interpret but, with our help, OEMs can take full advantage of the architecture.

