How to Protect Apps From Mobile Banking Security Threats
Watch our recent webinar to learn more.
Whilst we are used to hearing about big data breaches perpetrated against cloud systems, Mobile apps provide another, and often easer route in for attackers. Recent reports show that in Q2 of 2018 alone, 39% of all fraudulent transactions came from mobile apps. Compare that to only 5% three years before; that’s a 600% increase in attacks.
There’s also a significant increase in attacks based on malware, such as mobile banking trojans designed to steal credentials and money from customers’ bank accounts. According to a Lexis Nexis 2018 study, 46% of the fraud in financial services originates from mobile apps, and the recent record-breaking British Airways GDPR fine originating from a web and app attack.
Mobile Banking Security Threats
The breadth of attacks is also astounding; whether it’s sophisticated programming to find a hole in an application, or something simpler, malware is on the rise. Some of the most notable recent threats discovered by Lookout include:
- Bancmarstealer– first discovered by Lookout in 2015, this attack resurfaced in 2017, targeting over 60,000 financial institutions globally. Essentially, it’s an Android trojan that tricks the user into thinking that the malicious app is a legitimate banking application. It can also exploit the accessibility capabilities within Android to steal multi-factor authentication information.
- Deep attacks− these sophisticated attacks target the application logic. A recent example is the attack on WhatsApp where the code was modified. Once an attacker has breached the application code, they’re free to do almost anything within the context of the app – and for an app like WhatsApp that includes full data to microphone, camera, location, photos…
- Screen loggers and key loggers– these are more straightforward attacks that steal sensitive information from outside the target application. Such attacks have found a home in mobile apps, where they’ll sit on a phone and detect if there’s a banking app present. When the app is run, they’ll capture the information.
- Accessibility framework attacks− some attacks exploit the accessibility framework on devices. Attackers are weaponizing this, pretending to be the user to enter transactions and press buttons; for example, to disable a security feature.
- Overlay attacks− the attacker places a fraudulent window over a legitimate app on the device to gather user credentials, or to trick the user into disabling security settings to enable further attacks.
Perhaps the most frightening aspect of many of these attacks is how simple they are to instigate. The majority require no deep programming knowledge and malware toolkits make attacks frighteningly easy. It also means that no app – however small – is safe. There are numerous examples of malware toolkits that can be trivially repurposed by a “Script Kiddie” to retarget a new app.
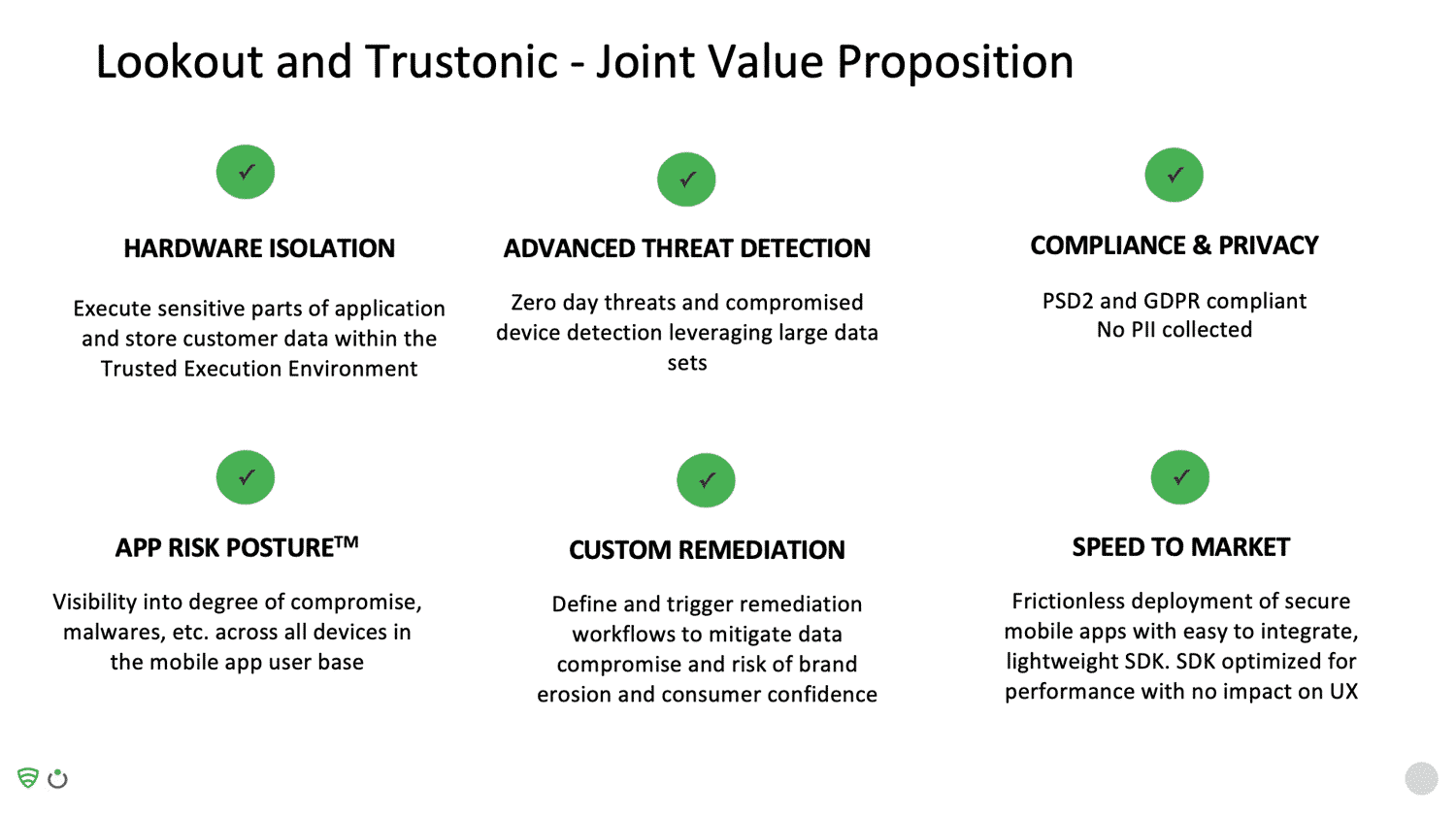
Mobile Banking Security Solution – Lookout & Trustonic’s Partnership Provides the Most Robust Banking & Fintech App Protection
About Trustonic
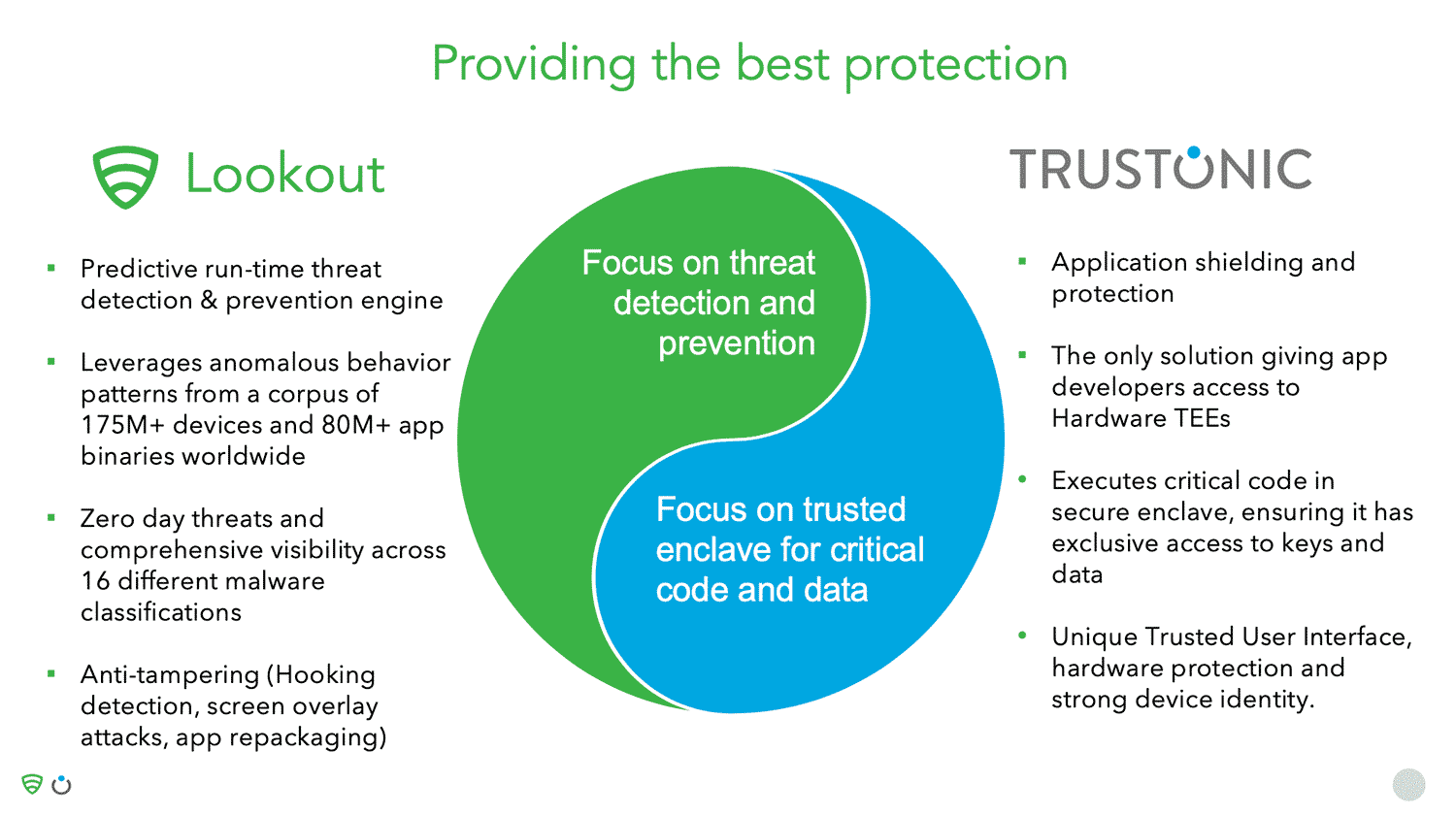
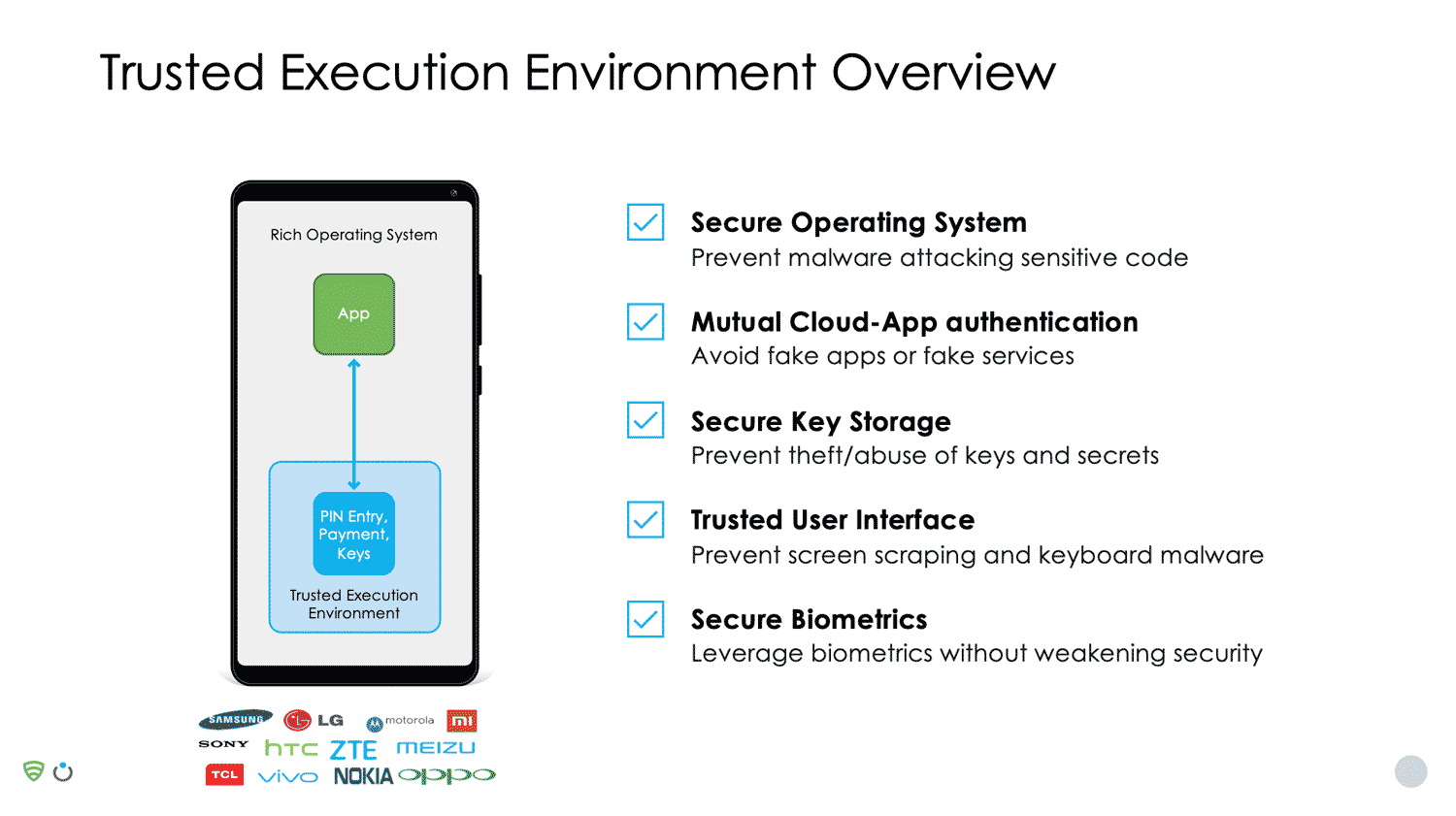
Trustonic’s secure operating system, known as a TEE (Trusted Execution Environment), has been integrated into 2 billion smart devices during manufacture. The technology is used in products by device OEMs, mobile network operators, and application developers.
The TEE is a secure OS that runs alongside the main Android OS. The security-sensitive part of the app (for example, authentication code or code that signs the transaction) runs in the safe environment of the TEE, rather than in Android. This isolates critical code and data, protecting it from attackers.
Using a TEE to protect critical code gives the best possible security on a device, however in general, TEEs are only accessible to device OEMs and not to 3rd party app developers.
Trustonic Application Protection (TAP) overcomes this limitation by providing access to the real hardware TEE on devices running Trustonic TEEs or those of our partner OEMs; and by providing a software TEE for all other devices. This combination enables the best possible security on every device, and Trustonic is the ONLY company to offer TEE access to app developers.
TAP takes care of the complexity of different TEEs and software protection tools and adds in higher level whole-app protection to compliment the TEE. TAP is certified to industry standards including FIPS, Common Criteria, and GlobalPlatform.
In addition to app protection itself, Trustonic also provide developers with high-level APIs, to provide a rich toolkit for cryptography, secure storage, strong app identity and Trusted User interface.
Strong app identity ensures that every app instance has its own X509 certificate. This means a back-end service can check a call came from legitimate code, and, if it’s from a device with a TEE, it can be traced back to the OEM’s factory, providing a chip-to-code trust.
Trustonic’s Trusted User Interface (TUI) enables TAP protected applications to access the screen and touch sensor with absolute hardware isolation. Whilst TUI is in use, Android literally has no access to either hardware device and absolutely no way to influence or detect what is displayed, or to simulate or intercept screen presses.
This makes the TUI ideal for processing confidential information such as sending secure messages or entering a PIN. For example, Samsung Pay uses a TUI for PIN entry, rather than relying on the Android OS. TUI goes well beyond PIN entry and can be used for any confidential display or input and can be fully branded.
About Lookout
Lookout are the market leaders in mobile app defence. Their technology complements the hardware-backed and software-based protection sides provided by Trustonic. Lookout examines the threat vectors on the device, analyses apps on the device, and undertakes a comprehensive analysis of app threats. Lookout provides:
- A predictive run-time threat detection and prevention engine
- The ability to leverage anomalous behaviour patterns from a corpus of 175M+ devices and 80M+ app binaries worldwide.
- Protection from zero-day threats and comprehensive visibility across 16 different malware classifications
- Anti-tampering measures (hooking detection, screen overlay attacks and app repackaging)
Lookout acquires about 100,000 apps on a daily basis from Google and the Apple play store, from crawling the dark web, and from third-party app stores. Static analysis is performed on the signature and binary analysis of apps on devices. Therefore, if a consumer downloads a malicious or side-loaded app, there’s every chance there’s a variation of it already in Lookout’s repository. If it’s a new app, Lookout do a binary acquisition of it; if it’s a new, malicious app, it becomes a zero-day threat.
With Lookout’s network of over 170M sensors, anomalies on devices are detected, providing protection from device-based threats as well as app-based threats, especially from hackers trying to root the device. If there’s a new zero-day threat, Lookout’s research team react quickly to identify new threats. These then become part of the malware family and, if there’s any variation, this is detected in real-time.
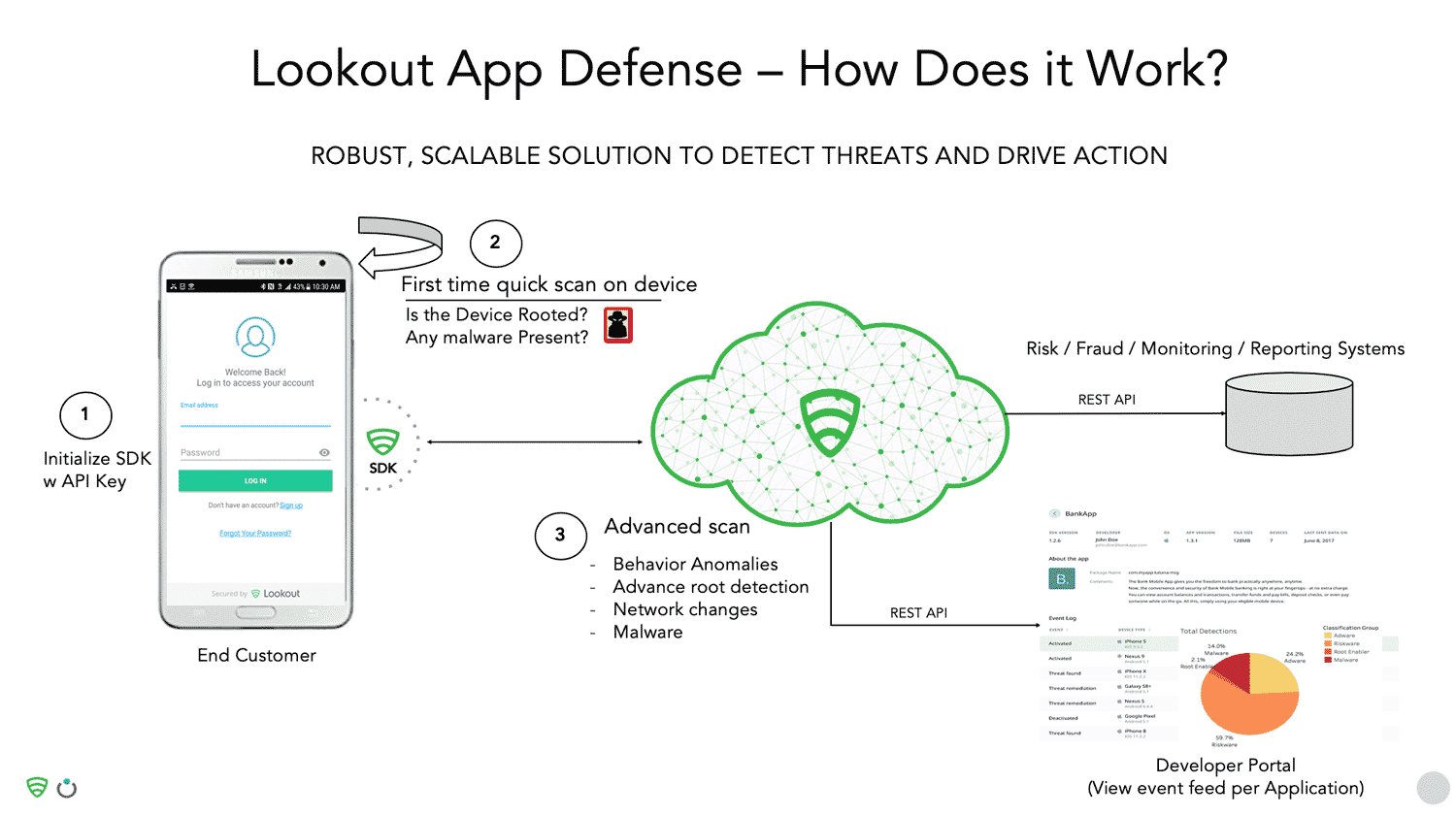
Lookout provides an App Defense SDK which checks the health of a device, checks the network, and performs an advanced scan. Detected threats are reported on the dashboard in real-time. Lookout also provides a developer portal so organizations that have multiple apps can go to a central place to register their app, obtain the key, debug their app, and get real-time visibility into threats. Restful APIs also allow you to take remediation steps, or feed this information into your own fraud and monitoring system.
Visibility is also provided into the app risk posture. The SDK helps to identify the percentage of devices that are rooted, have riskware, adware, and malware, and to take remedial action. Because Lookout have a repository of every family of malware known, they can classify malware at a deep level together with its severity.
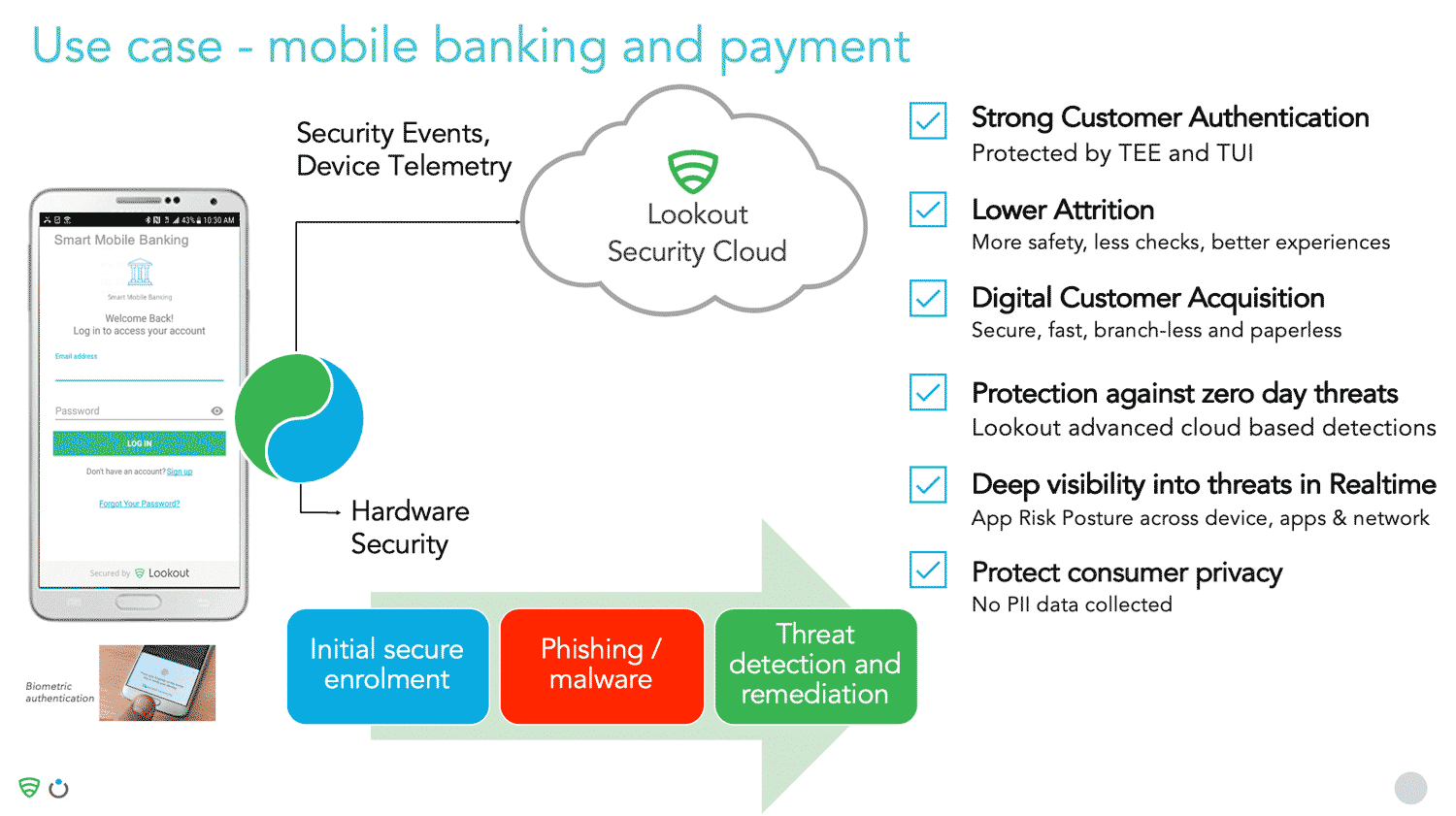
The joint solution in practice – Consider the following mobile banking and payment example
A user signs into their banking app using biometric authentication. At the point of biometric authentication, initial secure enrolment occurs. The UI in the TEE is secured using Trustonic’s technology to protect it in a hardware-encased environment.
As the user continues with authentication, Lookout scans the device to check for malicious apps and to ensure that the user isn’t connected to a malicious network, or using an insecure wireless connection. Security events and telemetry are passed in real-time to the Lookout security cloud for advanced analysis to look for zero-day threats and anomalies against apps already analysed by Lookout.
Therefore, the joint solution comprises of a combination of secure data protection, securing the interface during sign on, strong customer authentication, and continuous monitoring on the device to detect security threats.
Example customer deployment – A global 500 bank currently uses the 2 solutions in combination
The bank uses Lookout for the advanced root and jailbreak scenarios on Android and iOS, and for its ability to protect against phishing malware using two-factor-authentication, and to get visibility of real-time telemetry. In parallel, they use Trustonic’s TEE to store sensitive data and to protect the user interface operations.
This allows the bank to fully protect against all threats: app-based, device-based, and network-based.