Download the Whitepaper
The report outlines why a secure development lifecycle (SDL) – incorporating appropriate security testing, evaluation & certification – is essential to both achieve the levels of security and assurance defined by development teams, and meet industry, market and geographical requirements. It covers:
- The difference between Testing, Evaluation & Certification
- The main bodies defining and managing certification processes
- Mobile industry use cases – Apps and mobile devices for banking, payment, mPOS, government & identity
- Automotive & IoT use cases – Automotive DRM, in-vehicle infotainment (IVI), telematics and embedded IOT systems
A board-level concern
Security is no longer an afterthought for manufacturers of devices and app developers. Full consideration of threat scenarios, and the basic market expectation of a secure product, are now prerequisites. Not only for the development and deployment of mobile and edge devices like cars, wearables and healthtech, but also the apps and services that will run on them and ultimately, the end-user experience. As the number of attacks skyrockets, a standardized, best practice approach to device and embedded system security is the only way to ensure protection. This is where the secure development lifecycle (SDL) comes in.
What is a secure development lifecycle (SDL)?
A secure development lifecycle is a process by which security best practices are standardized for devices. This is achieved by capturing industry-standard security activities and packaging them so that they can be securely implemented. As product development must follow a secure development lifecycle, development teams have the option of building their own standardized processes or following pre-defined examples from companies such as Cisco and Microsoft.
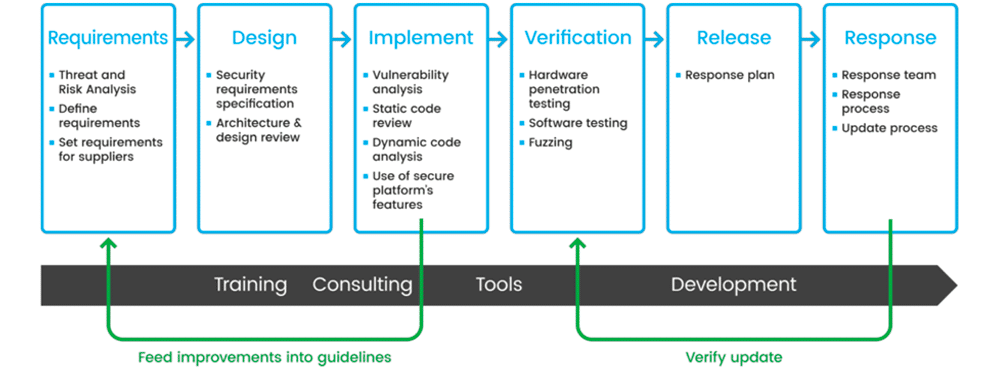
It is important that companies are able to guarantee that the latest design of their products conforms to a defined risk management plan. The only way to achieve this is through security testing, evaluation and certification as part of the SDL process.
What is the difference between security testing, evaluation & certification?
Overall, the SDL tests all the weakest points of a solution. These often lie between the boundaries of implemented security features. Hackers and fraudulent actors often think outside the box in order to circumvent security features. This is how security experts must think during mobile application vulnerability testing, evaluation and certification to determine how well a solution will be protected when under threat.
So, each adds important value to product development, but what’s the difference? Simply put, they are different processes that can be carried out at various stages of secure development and implementation.
Firstly, security testing is the process of exposing the possible different types of threats and attacks that could be carried out on a device. This can be done in an external laboratory or on-site, though it is considered best practice to involve and engage external security experts throughout testing.
Expert perspective:
“Security testing can demonstrate robustness, but is limited in its scope. Security evaluation uses a structured, holistic approach to assess the security robustness of a solution based on its intended usage, the design, implementation and often its development cycle.”
Security evaluation comes from an expert assessment of the product, its lifecycle and/or secure development process. This process must be carried out by a security laboratory and is based on industry standards and evaluation methodologies. The involvement of external parties during evaluation often adds significant knowledge and value to the process as internal teams often only have experience with a limited set of products.
To attain certification and provide assurance that a device or application meets industry-defined security benchmarks, a solution must be evaluated by an accredited laboratory against a set of formalized requirements and standards. For example, EMVCo certifies and evaluates products and services in line with the needs of the payments ecosystem and GlobalPlatform provides certification for secure platforms upon which solutions can be manufactured, like secure elements (SEs) and trusted execution environments (TEEs).
The certification body then provides written confirmation that a solution has passed all testing which can then be used by companies in the launch and marketing of their products. For some markets, like payments, certification is a requirement for market access.
Do I need to certify my device and applications?
The process of testing, evaluating and certifying products might seem like it’s slowing the launch of a new product, but this could not be further from the truth. In many cases certification is a requirement for a product to go to market. Even if this wasn’t the case, companies would be best advised to carry out the processes in order to identify possible vulnerabilities before a product goes to market.
Product launches can fail entirely based on security vulnerabilities and secure updates cannot be carried out without a trusted foundation within devices. This can have negative repercussions in terms of brand identity, not to mention limiting the profits that product launches are supposed to deliver.
Failed product launches are one thing, but data breaches are even more damaging to both brand equity and finances. Devices from in-car electronics to wearables now store more sensitive and personal data than ever, emphasizing the need for standardized security throughout device and application ecosystems.
Why are secure development lifecycles important to my business?
Ensuring that devices and applications are developed in line with a secure development lifecycle ensures that best practices are standardized. Without an SDL, products are more prone to being shipped with vulnerabilities, security mistakes can be repeated and identified too late and end-users have no active assurances that their device, and the data stored on it, is safe.
Business Benefits | |
| ✔ | Market access Certifications open doors to both geographical and vertical markets. For example, FIPS is a requirement for the U.S. marketplace and EMVCo is essential for payments. |
| ✔ | Security liability / risk management In vertical markets, like payments and content protection, certain parties are responsible for risk management and are liable in the event of an attack or a breach. |
| ✔ | Demonstrate robustness Security is often a differentiator for manufacturers and developers when selling products. Even where there are no defined specifications, tailored evaluation can be a way to prove worth to potential customers. |
| ✔ | Reputation protection A successful cyber-attack can cause major damage to your business. It can affect your revenues, as well as your business’ standing and consumer trust. |
| ✔ | Build additional services Service providers can use certified and trusted platforms as a foundation on which to build new value-added services because of higher trust. |
Eliminating risk and vulnerabilities: Certification ensures best-practice security and tangible operational benefits
Secure solutions are not designed and developed by accident. Trust is the result of careful planning and expertise. It is important to approach this not as a technical challenge, but as a process that is fundamental to the quality of your technology and the management of risk for both you and your end-users. All too often though, people forget that the right security can also be an enabler of both innovation and commercial value.
This is where certified trusted execution environment (TEE) technology is coming to the fore to support OEMs in securing devices and developers in bringing trust to their applications. Over the last five years, TEEs have become the de-facto hardware-backed security technology for smartphones, tablets, wearables and in-vehicle systems; protecting biometric authentication, user interfaces, premium content, cryptographic keys and related operations. The security platform has achieved this success because it can offer a hardware root-of-trust or security anchor within a device, while at the same time being more efficient than dedicated secure elements (SE’s) due to the extensive resource sharing with the device systems.
Security vs Functionality
Sometimes security is at odds with the functionality and usability of the product. If users experience friction in services, adoption or use will likely be impacted along with reputation. Security needs to be appropriate and in concert with the functionality and use case of the product. For this reason, there are multiple certified security components available which can be used in isolation or together to effectively protect and enrich devices.
This makes it a perfect technology to protect use cases including mobile payments, banking & acceptance, digital car key apps, in-vehicle infotainment (IVI) systems and mobile device protection for telcos.
As the world becomes more mobile-first, the spotlight will only brighten on security features. Being able to demonstrate a secure development lifecycle through certification is both a requirement and a strategic advantage for developers and manufacturers.
In collaboration with global security lab Riscure, Trustonic has published the first in a series of papers on the role and value of security testing, evaluation and certification in the design, development and launch of secure products and services.
Download the whitepaper
This paper will be valuable to:
- Development teams interested in implementing a secure development lifecycle to achieve security by design
- CEOs, CFOs and CPOs who want to protect critical services and brand reputation
- Product managers working to unlock key geographical and vertical markets and safeguard new products
For information on Trustonic’s hardware-backed device protection solutions visit our device security page. For advanced in-app protection, visit our application protection page and for information on our cybersecurity standards and certifications click here. Or email us at enquiries@trustonic.com.
For information about Riscure’s testing, evaluation and certifications services, email inforequest@riscure.com.

